 You might have been avoiding it until now – thinking that social networking (Facebook, MySpace, LinkedIn …) is just a passing trend, or it’s only used by teenagers, or people only use it to exchange photos and jokes. But, if you haven’t already realized it, social networks are here to stay, being used by people of all ages and social groups, and are having significant impacts (both positive and negative) on business. So, if you’re not already dealing with social networking as part of your security awareness training, you need to start now.
You might have been avoiding it until now – thinking that social networking (Facebook, MySpace, LinkedIn …) is just a passing trend, or it’s only used by teenagers, or people only use it to exchange photos and jokes. But, if you haven’t already realized it, social networks are here to stay, being used by people of all ages and social groups, and are having significant impacts (both positive and negative) on business. So, if you’re not already dealing with social networking as part of your security awareness training, you need to start now.
How Are Organizations Handling Social Networks?
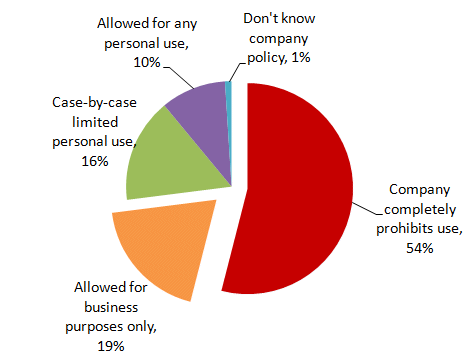
I hear a lot about social network use being banned in the workplace, so I was interested to see the results of a survey that asked just this question. From the results that they gathered, it would appear that most organizations either ban social network use entirely (54% of those surveyed), or limit use to business purposes only (another 19%). Only about 1/4 of organizations allow any degree of personal use.
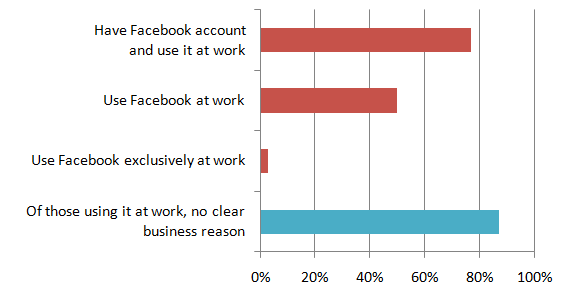
the USA with 100 or more employees carried out by Robert Half TechnologyHowever, many of your employees are probably using social networks – whether they’re banned in the workplace or not. Another recent survey showed how prevalent the use of one social network (Facebook) was, with nearly half of surveyed employees using Facebook during working hours with some using it for up to 2 hours each day.
Results of a survey by Nucleus Research.
When I talk with organizations, the primary reason for banning the use of social networks seems to be that they’re considered to be a significant productivity drain. And that’s probably true. But there’s also an element of concern about the security aspect, and the assumption that banning social networks in the workplace will solve that problem entirely.
| I’m here to tell you that’s NOT the case! |
The simple facts are:
- Unless you block access with web filtering tools, many of your staff will continue to use these sites in the workplace despite any bans.
- Staff using social networks outside the workplace still pose a significant threat.
Let’s look at this latter one a little more closely. In a recent blog post – Social Engineering Using Facebook – I wrote about how a security consultant was able to use information publically available from employees’ Facebook profiles to carry out an (authorized) attack on a company, and I noted that:
… banning social network use in the client’s workplace would probably have made very little difference since many of their employees – especially those expressing disaffection – would probably have continued to post the same information to Facebook from home.
It’s not just disaffected employees who are a problem. For example, you need to worry about IT staff posting technical questions to support groups that might give a hacker a hint about the systems that you’re running or a security hole you’re trying to fix, former-employees posting information to their LinkedIn profiles that detail the systems that they worked on when employed by you, executives providing enough information in interviews that a clever social engineer could impersonate them …
If you haven’t taught your employees to be careful about what they post, you’ve left a big hole in your defences.
What Should You Cover in Your Training?
So you’ve decided to grasp the bull by the horns and address social networking in your awareness training program. Wht should you cover?
Let’s start with the issues that are faced if social networks are being accessed from your company systems – either with or without your permission. (If you’ve blocked access to all social network sites, then you can probably skip this section). The good news is that they’re pretty much the same set of problems that you face with any Internet access by your staff – downloading infected files, clicking on links and popups that install spyware … but with the added complication that your employees might be lulled into a false sense of security because they’re “among friends”. Furthermore, there are more than 50,000 Facebook thid-party ‘applications’ (according to Facebook), and these applications aren’t all safe. And don’t forget basic email security since most social networks include their own messaging capabilities that could bypass antivirus tools installed on your email gateways.
So here are some of the topics that you’ll probably want to cover:
- What are viruses, worms, and spyware?
- Installation of malware through:
- Piggyback installation.
- Drive-by downloads.
- Browser add-ons.
- Pop-up ads.
- Fake antivirus and antispyware software.
- How to check (regular) hyperlinks.
- The dangers of “shortened” links.
- Using different passwords on social networks and work accounts.
- Basic email security – especially:
- Malware infections in attachments.
- Recognizing phishing and spear-phishing emails.
Now the issues that you’re going to have whether you ban social networking at work or not – your employees posting inappropriate and/or sensitive information online. They should be taught that:
- Privacy controls are critical. Anyone using a social network should take some time to make sure that they understand the privacy controls that it offers, and to make sure that you’ve set them up correctly to restrict access to your personal information – not just use the default settings.
- Information posted online should never include anything that might compromise the security of your organization. There are probably some obvious things to avoid (network information, anything about the security systems that have been installed …) but you’re going to have to help them understand what other things might be critical.
- They should also try to avoid posting information that might be used as a security question e.g. mother’s maiden name, pet’s name, name of high school. Posting this online could be making it easier for an identity thief.
- Make it clear that these restrictions apply as much to IT staff (and executives!) as other staff. In particular, you should point out how online support forums can be a treasure trove of information for hackers.
- Users of social networks should be selective when adding friends and connections, and (as far as is possible) try to ensure that they really are who they claim to be!
Final Thoughts
I just wanted to leave you with a few final thoughts:
- If you’re not already doing it, you should post or distribute, and have employees sign a policy that defines what they shouldn’t be posting – either as part of your Acceptable Use policy, or as a separate document. As well as making it clear how important social network security is, it might also provide you with some legal protection should the worst come to the worst.
- You might want to talk with your legal counsel about any restrictions that might be in place during company “quiet” periods that might affect what your employees can post online, and then include this in your training materials.
- As I noted in my earlier post – Social Engineering Using Facebook – if you’re responsible for an organization’s security, you really should be monitoring the social networking space as best you can to detect:
- Inappropriate posting of information relating to your organization by your organization’s staff
- The fraudulent use of your organization’s name/identity
- Bogus accounts set up in the name of your organization’s staff